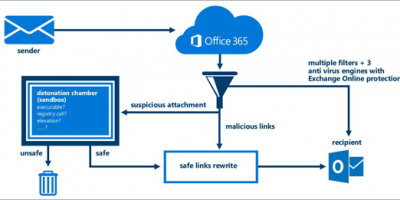
Approach
Before going into Office 365 Exchange Mailbox
After leaving Office 365 Exchange Mailbox.
Before going to the user mailbox.

Anti Malware Detection
Anti Phishing Detection
Attachment Filtering
Anti Spam Detection
Costs
US$230 per year for 10 users
(minimum purchase – 10 users)
USD$24 per year per user
(no minimum purchase)
Kaspersky Security for Microsoft Office 365
Kaspersky Security for Microsoft Office 365 is the smart choice for advanced, all-in-one threat protection for Microsoft Office 365’s communication and collaboration services – no vendor lock-in, no wasteful shelfware. Kaspersky Security for Microsoft Office 365 instantly stops the spread of malicious software, phishing, ransomware, spam and business email compromise (BEC) and requires no high-tech skills.
- Protects Microsoft Exchange Online, OneDrive, SharePoint Online and Teams
- Advanced threat protection: anti-phishing, anti-malware, anti-spam, unwanted attachments removal and protection on demand
- A significantly superior security performance with an AA rating in SE Labs’ email security test Download PDF report
Microsoft Defender for Office 365
Office 365 security builds on the core protections offered by EOP. EOP is present in any subscription where Exchange Online mailboxes can be found (remember, all the security products discussed here are Cloud-based).
You may be accustomed to seeing these three components discussed in this way:
| EOP | Microsoft Defender for Office 365 P1 | Microsoft Defender for Office 365 P2 |
|---|---|---|
|
Prevents broad, volume-based, known attacks.
|
Protects email and collaboration from zero-day malware, phish, and business email compromise.
|
Adds post-breach investigation, hunting, and response, as well as automation, and simulation (for training).
|